Security Assessment guide¶
This page serves as a guide for Mathesar team members to use when trying to decide the risk or severity of a (potential) vulnerability.
CVSS¶
For now, we’ll use the typical standard CVSS when trying to figure out whether a vulnerability is a big problem. For convenience, here’s a calculator with nice tooltips to explain how to fill it out:
https://nvd.nist.gov/vuln-metrics/cvss/v4-calculator
Assessment of issues and proposed features¶
If a team member notices a proposed feature or issue that we plan to implement, and that feature has some perceived security risk, that team member should do an assessment based on their understanding of the proposed feature using the calculator above. Only fill out the “Base Metrics” section.
When should I assess a feature or issue?¶
The goal should be to assess the feature after it’s actually specced out somewhat, but before it’s merged. If the issue is not yet fully specced out, the assessment may be a waste of time, e.g., if the person designing the feature has already though through mitigation options for any issues noticed. Subject to that constraint, however, earlier in the process is better.
Eventually, it’s likely that a quick assessment will be part of pulling any issue or proposed feature into a release cycle.
Example Assessment before mitigation¶
For example, consider File Upload support in forms. Here’s my attempt at an assessment:
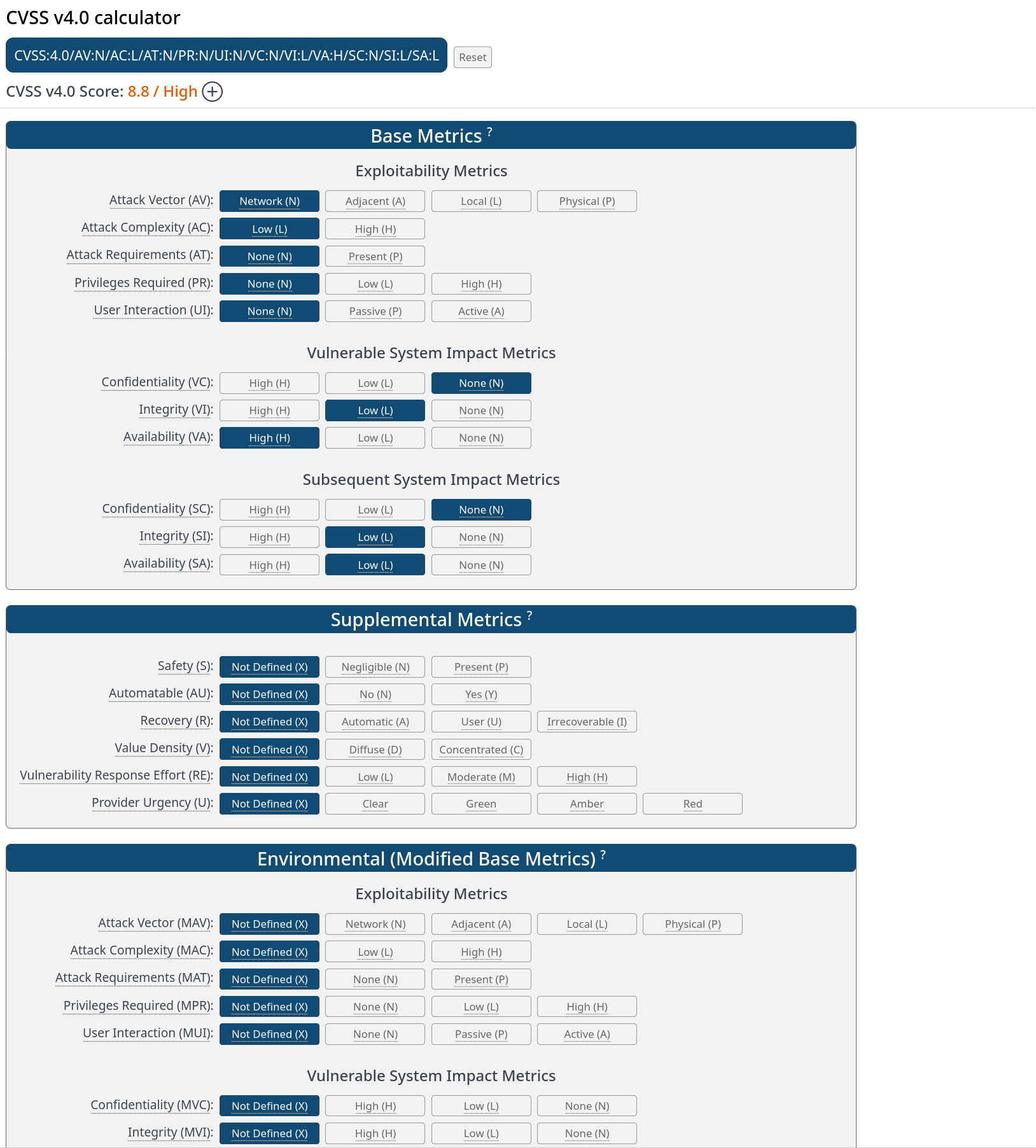
This assessment is based only on the issue description. If the score is “Medium” or “High”, or if the team is otherwise uncomfortable with the security implications, we then discuss mitigation options, and then reassess.
Review of PR related to or fixing issue with security implications¶
This is basically the same, except that if we can’t convince ourselves that the score for the CVSS system (Base Metrics only) is “Low” or “None”, we should not merge.
In general, any mitigation documentation or work should be included in the PR. It’s too easy to skip the follow-up PR and leave the vulnerability in.